- Cyber Safety
- Posts
- “The MFA Gap: Where Authentication Still Fails”
“The MFA Gap: Where Authentication Still Fails”
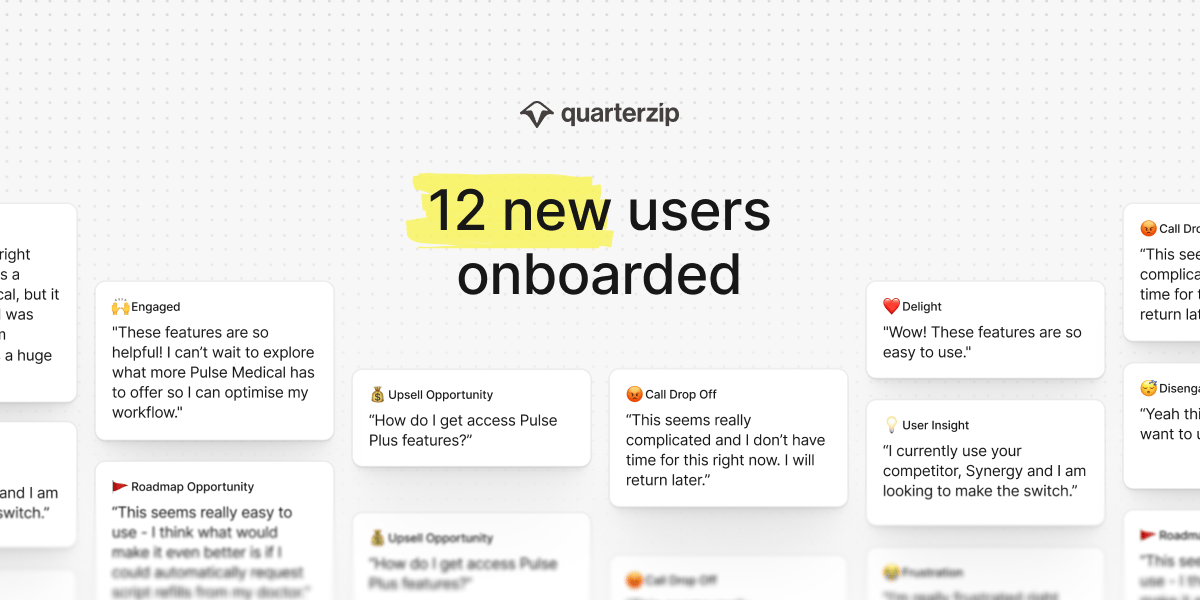
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
MFA Fatigue Attacks Exploit Human Behavior
Attackers trigger repeated MFA prompts until users approve out of habit or annoyance. This tactic bypasses protections without technical exploits. It’s social engineering at the push-notification layer.
Legacy Protocols Don’t Support Modern MFA
Old email clients and VPNs still rely on basic auth. These services often bypass MFA entirely. Attackers seek out legacy gaps that persist inside “secured” environments.
MFA Enrollment Is Spotty and Incomplete
Not all employees are enrolled — and contractors, interns, or vendors get exemptions. These accounts become targets of least resistance. Partial coverage creates total risk.
What 100K+ Engineers Read to Stay Ahead
Your GitHub stars won't save you if you're behind on tech trends.
That's why over 100K engineers read The Code to spot what's coming next.
Get curated tech news, tools, and insights twice a week
Learn about emerging trends you can leverage at work in just 10 mins
Become the engineer who always knows what's next
MFA Tokens Can Be Phished in Real-Time
Reverse proxy phishing sites capture both password and OTP in a single flow. Victims never know they gave up access. Adversaries use the credentials instantly before the token expires.
Device-Based MFA Can Be Spoofed or Cloned
Attackers intercept OTPs via malware, SIM swaps, or clipboard scraping. Some phones are rooted or jailbroken, making secure token storage unreliable. Hardware presence ≠ hardware trust.
“MFA Required” Doesn’t Mean “MFA Enforced”
Policies claim MFA is mandatory, but enforcement fails in practice. Admin accounts, service accounts, and fallback flows bypass enforcement. Audits often reveal more exceptions than rules.
Used by Execs at Google and OpenAI
Join 400,000+ professionals who rely on The AI Report to work smarter with AI.
Delivered daily, it breaks down tools, prompts, and real use cases—so you can implement AI without wasting time.
If they’re reading it, why aren’t you?