- Cyber Safety
- Posts
- “The Identity Mirage: When IAM Isn’t Enough”
“The Identity Mirage: When IAM Isn’t Enough”
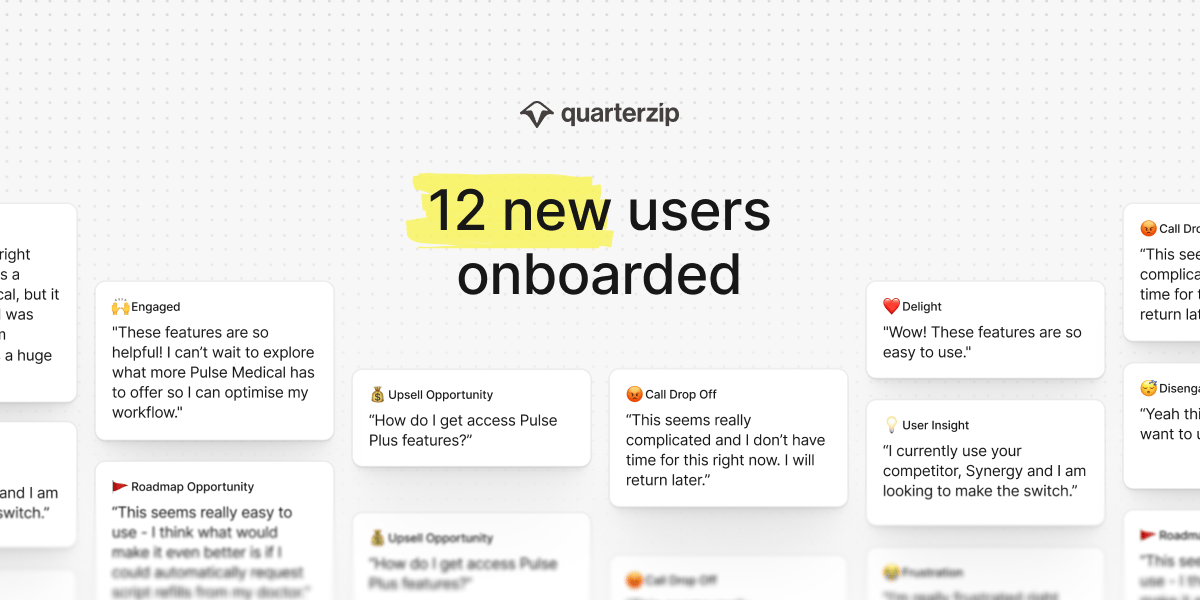
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
SSO Doesn’t Stop Credential Abuse
Single sign-on simplifies access but doesn’t verify intent. Once logged in, compromised accounts operate without suspicion. Lateral movement continues under the guise of legitimacy.
Role-Based Access Control Becomes Outdated Quickly
User roles rarely reflect real-time responsibilities. Employees change teams, but their access stays the same. Overprivileged accounts pile up without review.
Privilege Escalation Happens Inside the System
Attackers don’t need new credentials if they can elevate within. Misconfigured policies, forgotten groups, or dev tools grant admin access silently. IAM logs rarely show the nuance of escalation paths.
All the stories worth knowing—all in one place.
Business. Tech. Finance. Culture. If it’s worth knowing, it’s in the Brew.
Morning Brew’s free daily newsletter keeps 4+ million readers in the loop with stories that are smart, quick, and actually fun to read. You’ll learn something new every morning — and maybe even flex your brain with one of our crosswords or quizzes while you’re at it.
Get the news that makes you think, laugh, and maybe even brag about how informed you are.
Identity Federation Spreads Risk Across Tenants
Trust relationships between organizations expand the attack surface. Compromise in one tenant can cascade into others. Federated identity increases convenience and exposure equally.
MFA Enforcement is Inconsistent Across Services
Some apps require MFA, others don’t. Exceptions exist for legacy protocols, service accounts, or emergency users. Attackers target the weakest link in enforcement.
Deactivated Accounts Often Remain Active Elsewhere
Disabling a user in one system doesn’t propagate to others. Old VPNs, HR tools, or SaaS apps still accept the login. Dormant accounts become sleeper agents.
AI You’ll Actually Understand
Cut through the noise. The AI Report makes AI clear, practical, and useful—without needing a technical background.
Join 400,000+ professionals mastering AI in minutes a day.
Stay informed. Stay ahead.
No fluff—just results.