- Cyber Safety
- Posts
- “The False Promise of Air Gaps”
“The False Promise of Air Gaps”
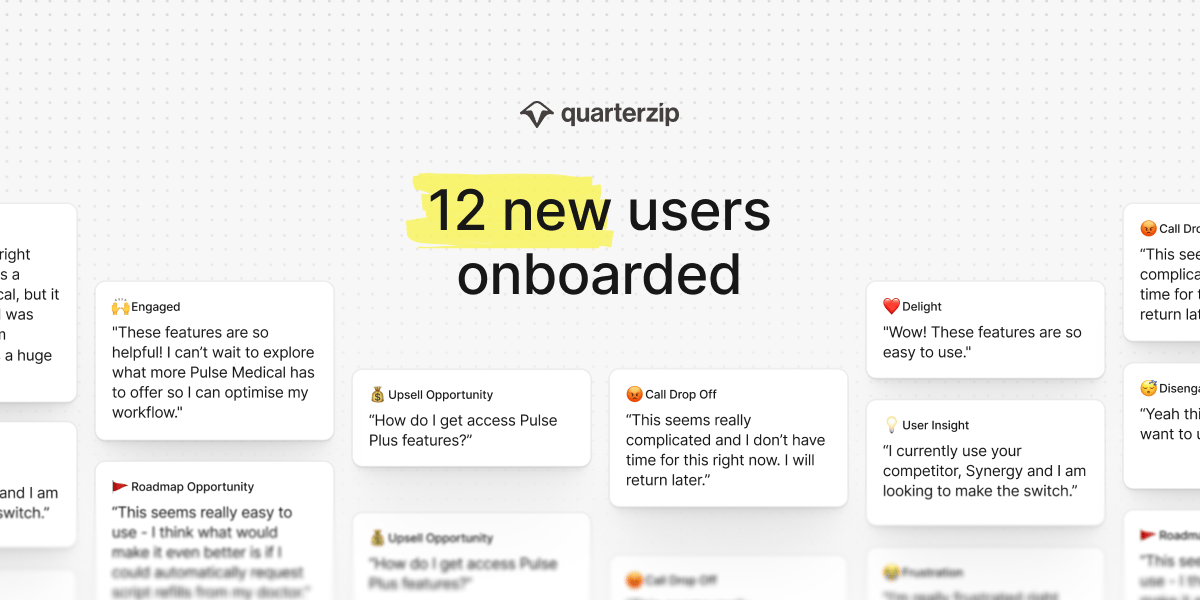
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Physically Isolated Doesn’t Mean Secure Anymore
Air-gapped networks still face compromise through firmware, USB, or RF bridges. Attackers no longer need internet access to infiltrate or exfiltrate. Isolation gives a false sense of invincibility.
USB Devices Are Trojan Horses in Secure Zones
Removable media are still used to transfer patches or logs. Even when scanned, malware can remain undetected in hidden partitions or firmware. These devices cross the gap attackers can't.
Insider Threats Are the Weak Link in Air-Gapped Systems
Human access brings software, updates, and intent — malicious or careless. Contractors or employees might carry infected tools unknowingly. Once inside, infections go undetected for years.
Free, private email that puts your privacy first
Proton Mail’s free plan keeps your inbox private and secure—no ads, no data mining. Built by privacy experts, it gives you real protection with no strings attached.
Lack of Monitoring Leaves Gaps Undiscovered
Air-gapped networks often lack logging, SIEM, or behavior analytics. Breaches can remain silent for years. The assumption of security replaces actual detection.
Covert Channels Use RF, Sound, or Light to Exfiltrate Data
Advanced attacks leverage acoustic, optical, or electromagnetic methods to bridge gaps. Malware modulates fan speed or keyboard LEDs to send signals. These side channels evade traditional defenses.
Patch Delays Leave Systems Perpetually Vulnerable
Updating air-gapped systems is manual and infrequent. Known vulnerabilities persist due to bureaucratic inertia. Attackers exploit well-documented flaws that should have been closed long ago.
Used by Execs at Google and OpenAI
Join 400,000+ professionals who rely on The AI Report to work smarter with AI.
Delivered daily, it breaks down tools, prompts, and real use cases—so you can implement AI without wasting time.
If they’re reading it, why aren’t you?