- Cyber Safety
- Posts
- “Replay & Reuse: When Old Sessions Become New Threats”
“Replay & Reuse: When Old Sessions Become New Threats”
Personalized Onboarding for Every User
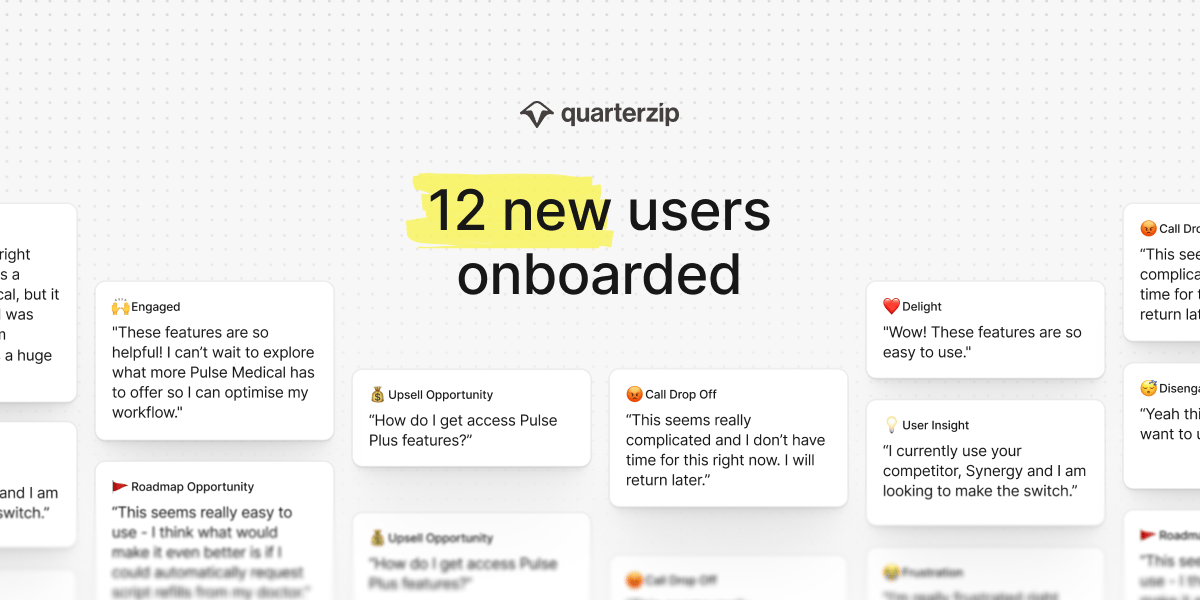
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Session Tokens Are Stolen and Replayed Without Detection
Attackers hijack active session cookies from browsers or memory. These tokens bypass login and MFA completely. Many systems lack replay detection or session uniqueness.
OAuth Tokens Grant Long-Term Access Without Alerts
OAuth credentials can last weeks or months, often with broad permissions. Compromised tokens go unnoticed unless revoked manually. APIs trust these tokens too blindly.
API Keys Are Reused Across Projects Without Rotation
Developers copy the same keys across apps, scripts, or repos. Once leaked, the same key grants access to multiple systems. Few teams enforce key expiration or scope limits.
All the news that matters to your career & life
Hyper-relevant news. Bite-sized stories. Written with personality. And games that’ll keep you coming back.
Morning Brew is the go-to newsletter for anyone who wants to stay on top of the world’s most pressing stories — in a quick, witty, and actually enjoyable way. If it impacts your career or life, you can bet it’s covered in the Brew — with a few puns sprinkled in to keep things interesting.
Join over 4 million people who read Morning Brew every day, and start your mornings with the news that matters most — minus the boring stuff.
QR Code Logins Can Be Spoofed and Reused
QR login links allow easy sign-in from mobile, but they carry embedded session secrets. These links can be intercepted, reused, or phished. Most apps lack expiration or rate limits on them.
Forgotten Access Tokens Survive Account Deletion
Revoking a user doesn’t always kill their associated tokens. Background processes, integrations, or apps still function. Attackers use these zombie tokens to re-enter quietly.
Legacy Authentication Flows Accept Replay by Design
Old SSO flows and legacy protocols weren’t built with modern threat models. They accept repeated credentials or stale handshakes. Attackers exploit them in automated campaigns.
Stop Drowning In AI Information Overload
Your inbox is flooded with newsletters. Your feed is chaos. Somewhere in that noise are the insights that could transform your work—but who has time to find them?
The Deep View solves this. We read everything, analyze what matters, and deliver only the intelligence you need. No duplicate stories, no filler content, no wasted time. Just the essential AI developments that impact your industry, explained clearly and concisely.
Replace hours of scattered reading with five focused minutes. While others scramble to keep up, you'll stay ahead of developments that matter. 600,000+ professionals at top companies have already made this switch.