- Cyber Safety
- Posts
- “OT & ICS: When the Factory Floor Becomes the Attack Surface”
“OT & ICS: When the Factory Floor Becomes the Attack Surface”
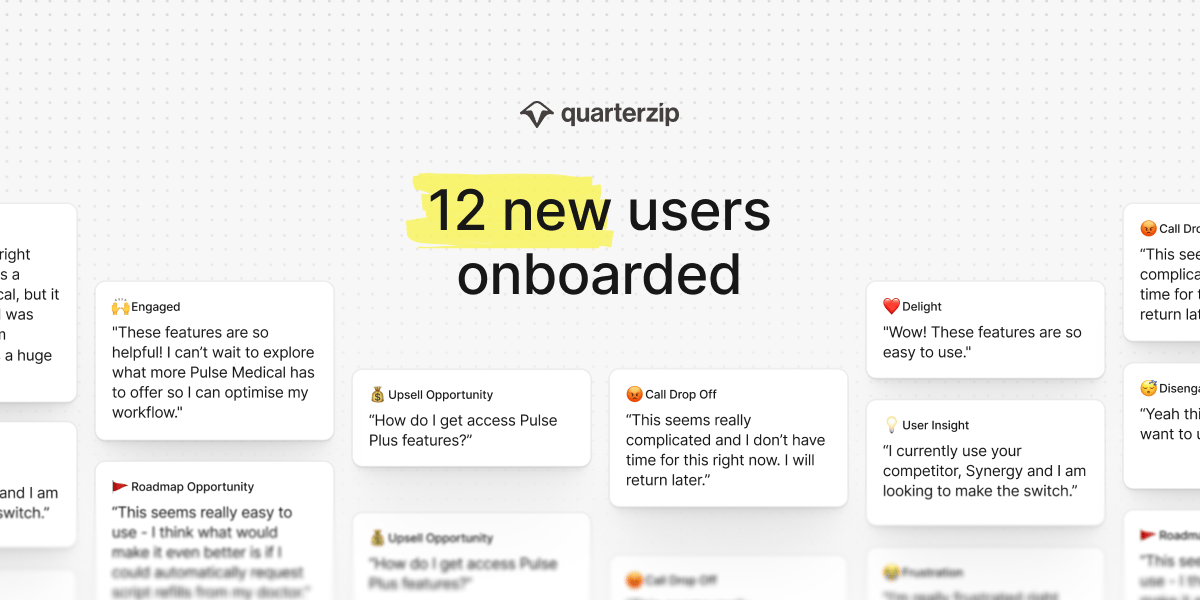
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
IT and OT Networks Are Poorly Segmented
Many organizations still run flat networks connecting office systems with industrial controls. This allows malware from emails to jump directly into factory systems. A single breach can disrupt both corporate and operational environments.
Legacy PLCs and SCADA Devices Use Default Credentials
Industrial equipment often runs unpatched firmware from a decade ago. Default logins like “admin/admin” remain unchanged due to access limitations. These weaknesses are publicly known and easily exploited.
Industrial Protocols Are Unauthenticated and Unencrypted
Protocols like Modbus and BACnet were designed for isolated environments. Today, they're deployed on IP networks without encryption or access control. Attackers can spoof commands and manipulate sensors or actuators.
Proton Mail gives you a clutter-free space to read your newsletters — no tracking, no spam, no tabs.
Remote Access Tools in OT Aren’t Hardened
Vendors often use TeamViewer, RDP, or proprietary access portals for remote maintenance. These are rarely monitored or logged. A stolen vendor credential can offer full plant control.
USB Devices Still Introduce Malware in Industrial Zones
Portable drives are used to update firmware or transfer logs in air-gapped environments. Infected USBs can introduce persistent threats into isolated systems. Once inside, detection is nearly impossible without OT-specific tools.
Visibility Gaps Exist in Most ICS Security Stacks
Traditional IT security tools can’t see or interpret OT protocols. Alerts go unnoticed, and logs aren’t retained. Without deep packet inspection tailored to ICS, attacks remain hidden.
The Gold standard for AI news
AI will eliminate 300 million jobs in the next 5 years.
Yours doesn't have to be one of them.
Here's how to future-proof your career:
Join the Superhuman AI newsletter - read by 1M+ professionals
Learn AI skills in 3 mins a day
Become the AI expert on your team