- Cyber Safety
- Posts
- “Logging Illusions: What Your SIEM Doesn’t See”
“Logging Illusions: What Your SIEM Doesn’t See”
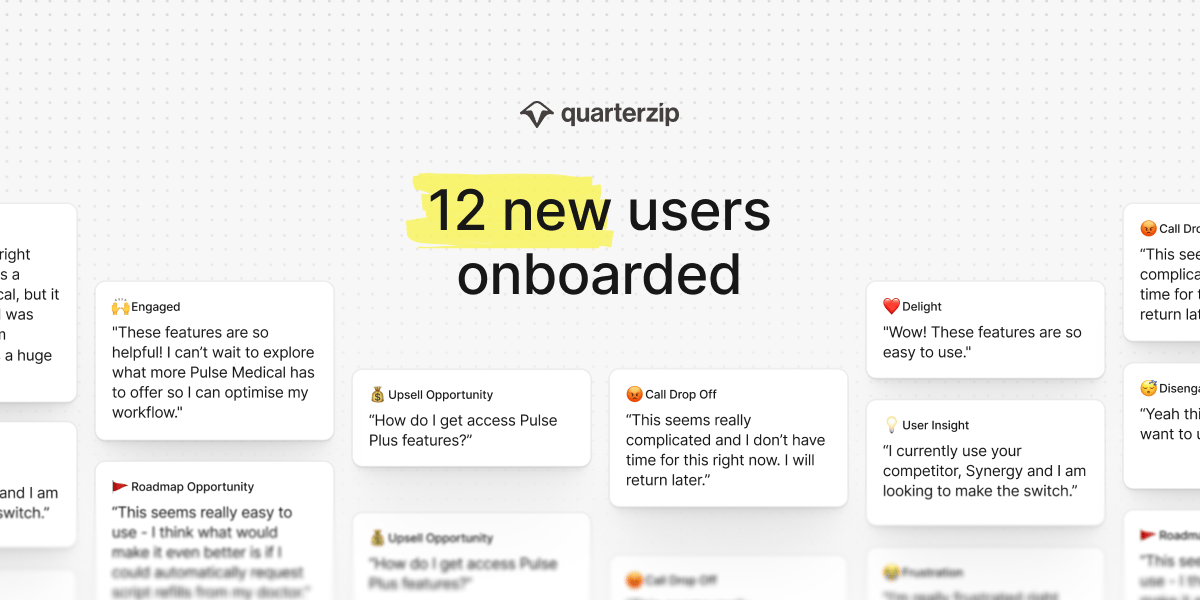
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Critical Events Are Silenced by Logging Misconfigurations
Many systems generate logs locally but never forward them to the SIEM. Disk space, agent errors, or filter rules drop key events. Security teams operate blind, thinking they’re fully covered.
Cloud Logs Are Stored Separately and Forgotten
AWS CloudTrail, Azure Monitor, and GCP Audit Logs live in different silos. Analysts miss incidents when data isn’t unified. Attackers exploit this disconnection to avoid correlation.
Log Retention Policies Are Too Short to Catch Slow Attacks
30-day retention windows miss multi-phase campaigns. By the time the breach is detected, evidence is gone. Long-term storage is seen as a cost — until it’s too late.
Free, private email that puts your privacy first
Proton Mail’s free plan keeps your inbox private and secure—no ads, no data mining. Built by privacy experts, it gives you real protection with no strings attached.
Alert Fatigue Leads to Blind Spots in Tuning
Excessive false positives cause teams to suppress entire categories of alerts. These tuning decisions often go undocumented. Real threats slip through the gaps left behind.
Applications Mask Failures Behind 200 OK Responses
APIs and web apps often return successful status codes even when errors occur. Security tools miss these anomalies without deep inspection. Attackers exploit these silent failures for stealth.
Endpoint Logs Don’t Cover Lateral Movement or Exfiltration
Basic logging captures logins, but not how accounts are used afterward. No visibility into data access, copying, or transfers. Lateral movement remains invisible without enhanced telemetry.
Choose the Right AI Tools
With thousands of AI tools available, how do you know which ones are worth your money? Subscribe to Mindstream and get our expert guide comparing 40+ popular AI tools. Discover which free options rival paid versions and when upgrading is essential. Stop overspending on tools you don't need and find the perfect AI stack for your workflow.