- Cyber Safety
- Posts
- “Invisible Intrusions: Fileless & Living-off-the-Land Attacks”
“Invisible Intrusions: Fileless & Living-off-the-Land Attacks”
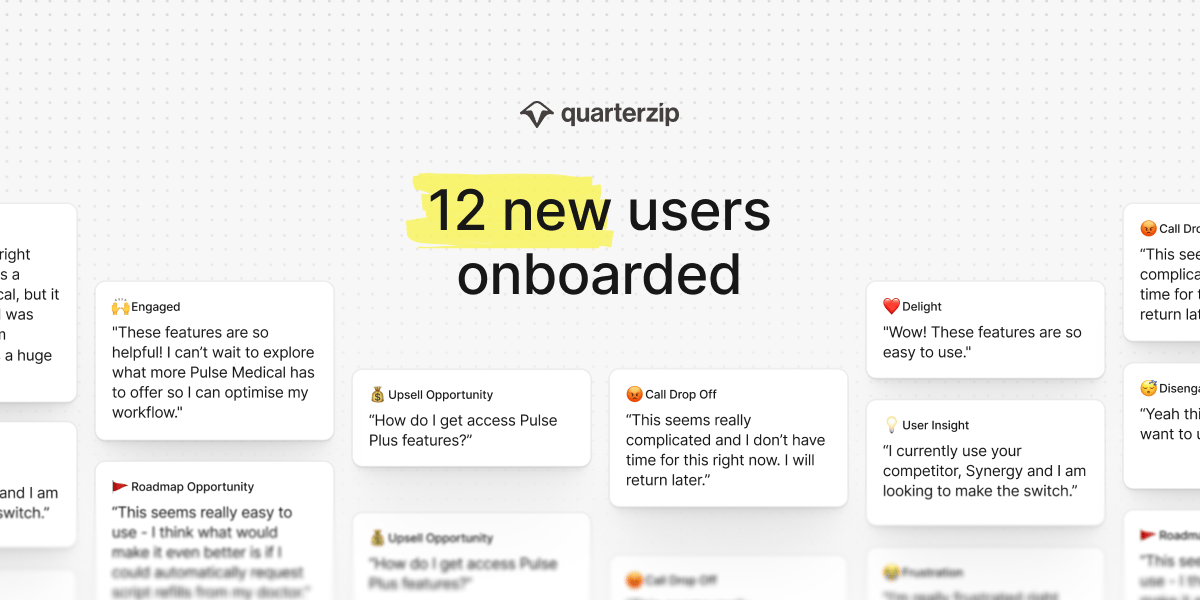
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Fileless Malware Operates Fully In-Memory to Evade Detection
No files are dropped on disk, avoiding traditional antivirus. Attackers use PowerShell, WMI, or LOLBins already present in the system. These actions are nearly invisible unless behavior analytics are in place.
Native OS Tools Are Weaponized for Malicious Persistence
Built-in commands like certutil, mshta, or regsvr32 are used to download or run payloads. Since they’re signed and trusted, they bypass many security controls. Monitoring their usage is critical for defense.
Registry and Scheduled Tasks Are Used for Stealthy Access
Attackers plant persistence hooks in obscure registry keys or create hidden scheduled tasks. These survive reboots and go unnoticed by most antivirus tools. Even forensic analysts often miss them during incident response.
Free, private email that puts your privacy first
Proton Mail’s free plan keeps your inbox private and secure—no ads, no data mining. Built by privacy experts, it gives you real protection with no strings attached.
DLL Hijacking Exploits Application Loading Behaviors
Applications load DLLs based on search order, not integrity. Attackers drop malicious DLLs into expected directories. The app executes them unknowingly with its full privileges.
Reflective Code Injection Keeps Payloads Off Disk
Payloads are injected directly into memory of legitimate processes. This technique avoids writing any executable code to disk. Security tools must rely on in-memory analysis to detect such activity.
Exfiltration Happens Directly From RAM or Trusted Binaries
Sensitive data is collected and sent out using trusted system processes. Since no new binaries are used, traffic appears normal. Without deep packet inspection or EDR, exfiltration goes undetected.
Wall Street’s Morning Edge.
Investing isn’t about chasing headlines — it’s about clarity. In a world of hype and hot takes, The Daily Upside delivers real value: sharp, trustworthy insights on markets, business, and the economy, written by former bankers and seasoned financial journalists.
That’s why over 1 million investors — from Wall Street pros to Main Street portfolio managers — start their day with The Daily Upside.
Invest better. Read The Daily Upside.