- Cyber Safety
- Posts
- “Edge AI: Vulnerabilities at the Device Layer”
“Edge AI: Vulnerabilities at the Device Layer”
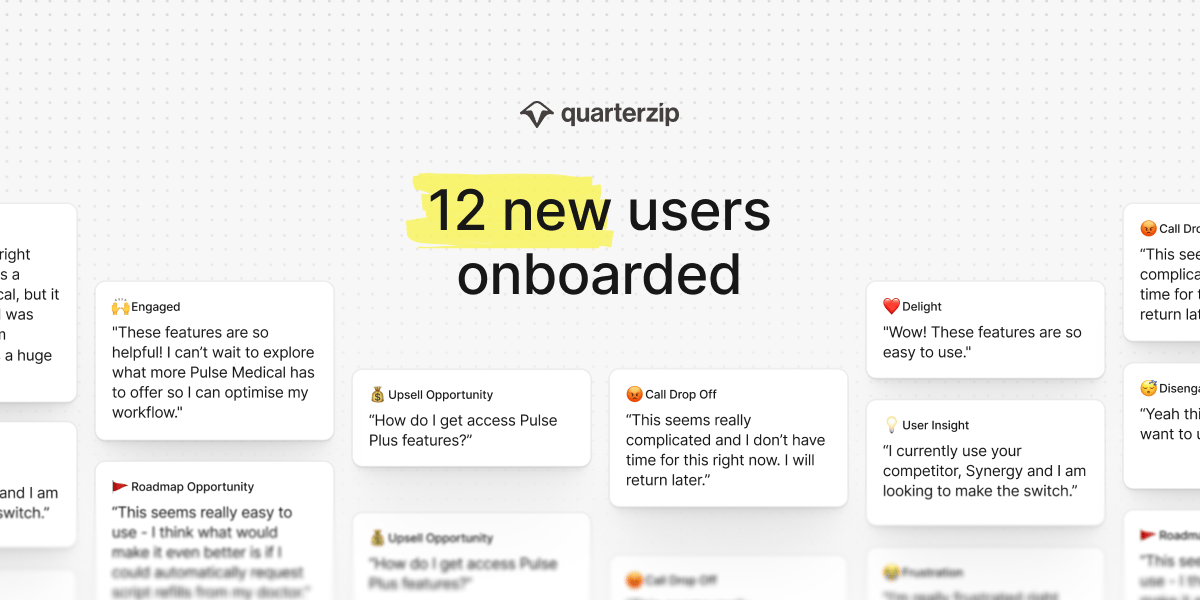
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Edge Devices Store and Leak Embedded Model Logic
AI models deployed on mobile, IoT, or industrial devices are often stored in plain form. Reverse-engineering these models reveals decision logic and training data. Attackers exploit this to create targeted adversarial inputs.
Firmware Updates Lack Cryptographic Protections
Many edge devices allow firmware changes without signature verification. Attackers can install modified firmware containing backdoors. Once infected, these devices become long-term footholds.
Power and Performance Constraints Disable Security Logging
Edge systems limit logging to preserve battery and speed. This reduces visibility into local attacks or misuse. Intrusions often go unnoticed due to monitoring trade-offs.
Free, private email that puts your privacy first
Proton Mail’s free plan keeps your inbox private and secure—no ads, no data mining. Built by privacy experts, it gives you real protection with no strings attached.
Physical Access Equals Full Compromise at the Edge
Devices in public or semi-secure areas can be physically accessed. USB, SD cards, or debug ports provide complete access. Security depends heavily on location — a weak barrier.
Model Drift Happens Without Central Oversight
Edge models sometimes retrain or adapt based on local data. Without central control, behavior diverges dangerously from the intended design. This creates inconsistent and unpredictable outcomes.
Connectivity Gaps Leave Devices Vulnerable to Delayed Patches
Many edge devices only connect occasionally or over low-bandwidth links. Patches are delayed or never applied. Attackers target these devices knowing their window of exposure is long.
Choose the Right AI Tools
With thousands of AI tools available, how do you know which ones are worth your money? Subscribe to Mindstream and get our expert guide comparing 40+ popular AI tools. Discover which free options rival paid versions and when upgrading is essential. Stop overspending on tools you don't need and find the perfect AI stack for your workflow.