- Cyber Safety
- Posts
- Cybersecurity Crisis: How Teams Are Adapting Fast in a World of Rapid Vulnerabilities!
Cybersecurity Crisis: How Teams Are Adapting Fast in a World of Rapid Vulnerabilities!

Stellantis N.V. is grappling with significant challenges stemming from supply chain vulnerabilities and the electric vehicle transition. Key points include:
• Reliance on a global supply chain exposes the company to potential disruptions.
• Geopolitical tensions, natural disasters, and pandemics pose ongoing risks.
• Transitioning to electric vehicles demands hefty investment and adaptation.
These factors could hinder Stellantis’s market position and profitability, leading analysts to project an average stock price target of $11.26, suggesting a potential 17.91% upside. As the landscape evolves, how Stellantis navigates these issues will be crucial.
Fact-based news without bias awaits. Make 1440 your choice today.
Overwhelmed by biased news? Cut through the clutter and get straight facts with your daily 1440 digest. From politics to sports, join millions who start their day informed.

Veeam has issued urgent updates to fix critical vulnerabilities in its Backup & Replication (VBR) software. Code named CVE-2025-23121, this flaw allows domain-joined installations to be threatened by remote code execution (RCE) attacks.
Key Highlights:
• Affects Veeam Backup & Replication version 12 and above.
• Exploitable by any authenticated domain user with low-complexity methods.
• Previous vulnerabilities have facilitated ransomware attacks, targeting backup servers.
Organizations are urged to patch now and strengthen security measures, like using two-factor authentication, to protect their data.

The cybersecurity landscape is evolving rapidly, demanding an urgent response from security teams. Key highlights include:
• Over 28% of vulnerabilities exploited within one day of disclosure.
• A staggering 40,003 CVEs reported in 2024, a 39% increase from 2023.
• INE Security’s Skill Dive platform offers hands-on practice with real vulnerabilities.
Traditional methods can't keep pace with quickening attacks. Skill Dive's labs provide a practical approach, empowering professionals to anticipate threats and respond confidently. The platform focuses on real-world scenarios, ensuring teams are prepared for emerging cyber challenges. Stay ahead of the game with continuous updates and immersive training!
Find out why 1M+ professionals read Superhuman AI daily.
In 2 years you will be working for AI
Or an AI will be working for you
Here's how you can future-proof yourself:
Join the Superhuman AI newsletter – read by 1M+ people at top companies
Master AI tools, tutorials, and news in just 3 minutes a day
Become 10X more productive using AI
Join 1,000,000+ pros at companies like Google, Meta, and Amazon that are using AI to get ahead.
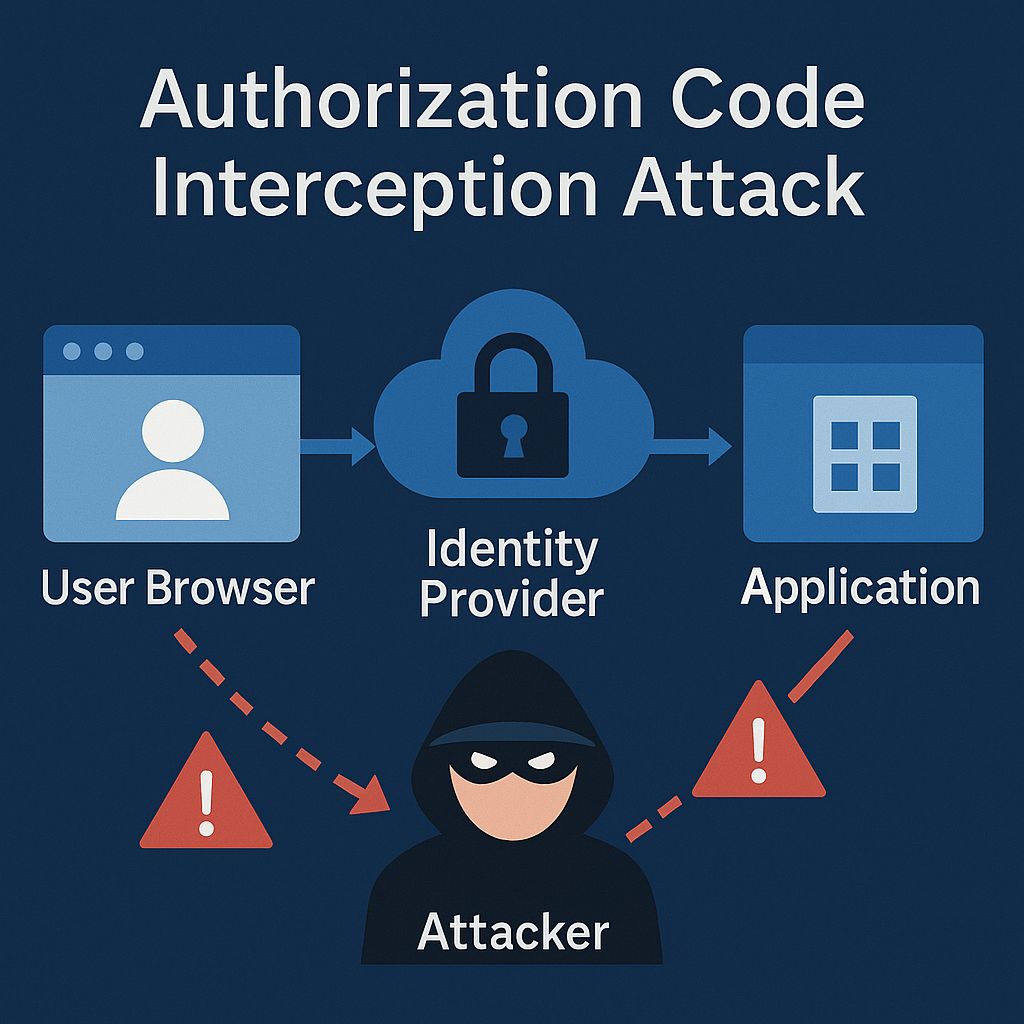
In the world of Single Sign-On (SSO), protecting your authentication flow is crucial. Here's a peek at some common SSO vulnerabilities and how to mitigate them:
• OAuth Issues: Code interception and redirect URI manipulation can create serious security risks.
• SAML Vulnerabilities: Replay and assertion wrapping attacks can compromise user information.
Implementing robust strategies like PKCE for OAuth, strict URI validation, and proper signature validation for SAML is essential. Regular security audits and continuous monitoring can further strengthen your defenses, ensuring trust remains intact in your authentication ecosystem.

In "The Security Vulnerabilities We Built In," Radoslaw Madej highlights the emerging risks posed by AI agents. These systems, designed to assist, face exploitation through seemingly harmless prompts, turning them into unwitting accomplices in cyberattacks. Key points include:
• AI agents can be manipulated using innocuous language commands.
• Traditional security measures often fail against language-based attacks.
• Organizations must audit AI access, limit permissions, and enhance monitoring.
As LLMs evolve, they present both challenges and opportunities, urging proactive measures for a secure future in cybersecurity.

