- Cyber Safety
- Posts
- “Compliance Creep: Blind Spots in Regulation & Audit”
“Compliance Creep: Blind Spots in Regulation & Audit”
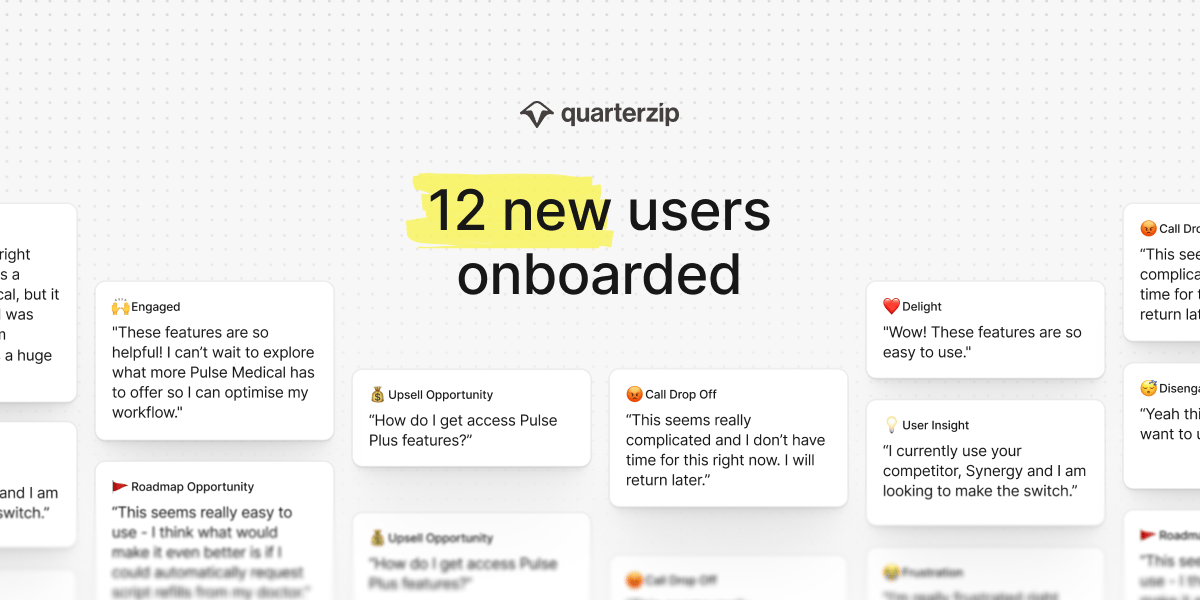
Personalized Onboarding for Every User
Quarterzip makes user onboarding seamless and adaptive. No code required.
✨ Analytics and insights track onboarding progress, sentiment, and revenue opportunities
✨ Branding and personalization match the assistant’s look, tone, and language to your brand.
✨ Guardrails keep things accurate with smooth handoffs if needed
Onboarding that’s personalized, measurable, and built to grow with you.
Audit Findings Often Remain Unresolved for Years
Security audits reveal critical gaps, but remediation gets deprioritized. Old findings persist across multiple cycles, becoming long-term risks. Attackers exploit these ignored weaknesses before internal teams do.
Overlapping Frameworks Cause Control Conflicts
Companies juggling GDPR, SOC2, NIS2, and HIPAA face contradictions. A control that satisfies one regulation may violate another. Without a unified compliance map, teams apply inconsistent security measures.
Shadow IT Continues to Escape Audit Scope
Employees use unapproved apps for convenience — file sharing, messaging, automation. These tools operate outside formal reviews and risk assessments. As a result, compliance coverage is only partial and outdated.
Free, private email that puts your privacy first
Proton Mail’s free plan keeps your inbox private and secure—no ads, no data mining. Built by privacy experts, it gives you real protection with no strings attached.
Third-Party Subcontractors Introduce Silent Gaps
Vendors often subcontract further without full disclosure. These extended chains bypass your direct compliance controls. When data leaks, it’s unclear where responsibility lies.
Audit Trails Lack Integrity or Completeness
Logs are overwritten too quickly or not collected at all. Timestamps are unsynchronized, and log tampering is undetectable. This hinders forensics and undermines regulatory claims.
Policy Declarations Don’t Match Actual Risk Appetite
Companies publish strong-sounding security policies without operational follow-through. Stated zero-tolerance for breaches isn’t reflected in resourcing or tooling. Compliance becomes performative instead of protective.
Become An AI Expert In Just 5 Minutes
If you’re a decision maker at your company, you need to be on the bleeding edge of, well, everything. But before you go signing up for seminars, conferences, lunch ‘n learns, and all that jazz, just know there’s a far better (and simpler) way: Subscribing to The Deep View.
This daily newsletter condenses everything you need to know about the latest and greatest AI developments into a 5-minute read. Squeeze it into your morning coffee break and before you know it, you’ll be an expert too.
Subscribe right here. It’s totally free, wildly informative, and trusted by 600,000+ readers at Google, Meta, Microsoft, and beyond.