- Cyber Safety
- Posts
- After the Breach: Missed Steps, Sync Drift & Trust Fatigue
After the Breach: Missed Steps, Sync Drift & Trust Fatigue
In Partnership With

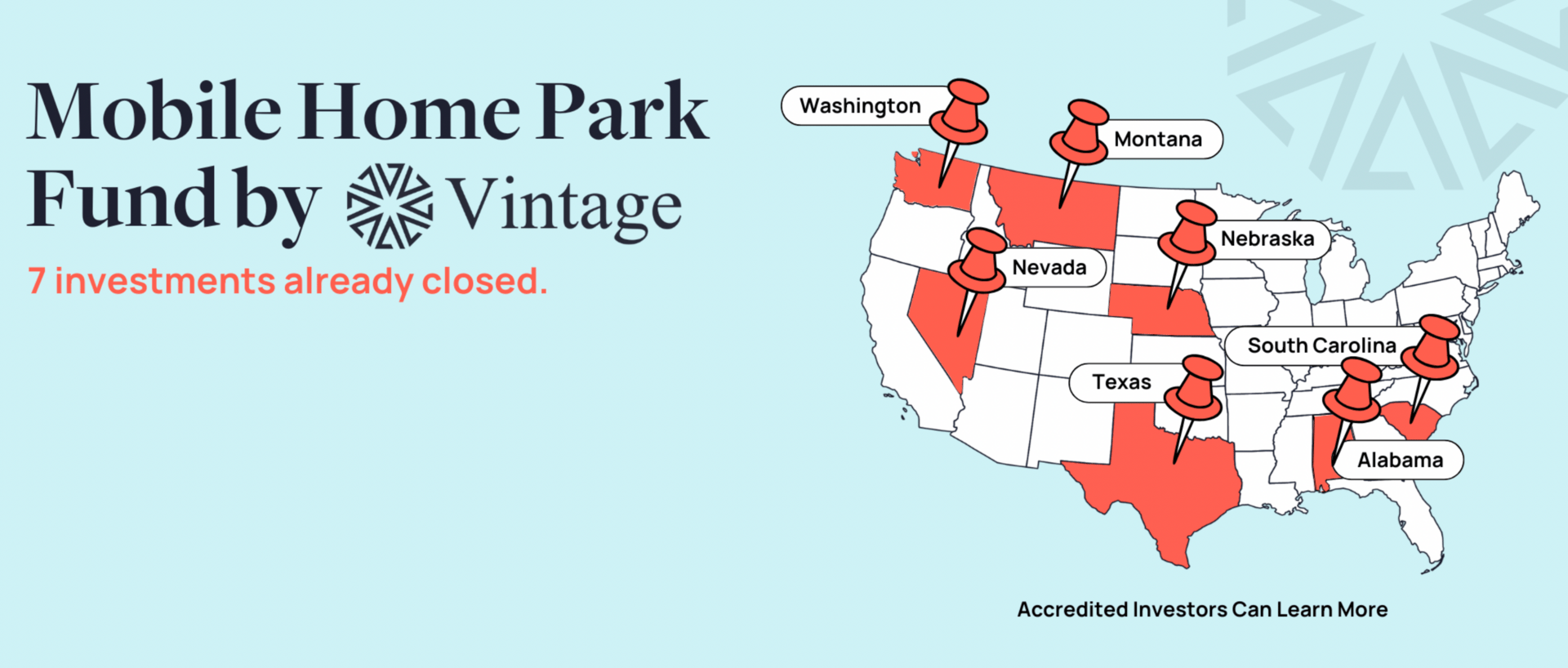
Invest in recession-resilient Mobile Home Parks with Vintage Capital. Invest direct or in a fund of 20+ underlying assets. 1031s are also available. Access stable, income-generating properties with consistent demand and low tenant turnover.
Now is the time to act: Current market conditions are creating opportunities to acquire properties at attractive valuations.
Our fund targets a 15%-17% IRR and makes monthly distributions, which provides a steady income stream alongside strong upside potential and tax-efficient benefits.
Why Mobile Home Parks?
Recession-Resilient: Affordable housing demand drives stable returns in any economy
High Tenant Retention: The average MHP tenant stays 10-12 years (compared to 2-3 in Multifamily)
Proven Expertise: $100MM+ track record in mobile home park investments.
Tax-Smart Investing: Bonus depreciation offers tax advantages.
Automation Workflows Are Being Weaponized by Insiders
Rogue employees are leveraging Zapier, Make.com, and internal automation tools to exfiltrate data, clone alerts, or redirect logs—without triggering security controls.
Audit automation platforms for flows tied to sensitive systems. Require peer review, label critical workflows, and alert on high-risk automation patterns.
Old VPN Clients Are Still in Use—With Known CVEs
While companies have upgraded VPN infrastructure, many remote users are still running outdated clients that expose the network to known exploits.
Force version control at login, audit installed clients, and auto-deprecate old versions with phased offboarding prompts.
Compromised Email Rules Are Staying Hidden Post-Breach
Even after remediation, attackers often leave malicious inbox rules intact—auto-forwarding sensitive emails or silently deleting password change notices.
Include mailbox rule checks in all IR processes. Notify users of rule changes and log edits to inbox settings.
Productivity Apps Are Syncing Sensitive Data to Unauthorized Devices
Tools like Notion, Trello, and Evernote sync offline data to personal laptops and phones by default—creating unsanctioned data copies.
Enforce device trust policies for SaaS access, disable offline mode in unmanaged environments, and classify shared boards by sensitivity.
The Gold standard for AI news
AI will eliminate 300 million jobs in the next 5 years.
Yours doesn't have to be one of them.
Here's how to future-proof your career:
Join the Superhuman AI newsletter - read by 1M+ professionals
Learn AI skills in 3 mins a day
Become the AI expert on your team
Push Notification Fatigue Is Creating Approval Drift
Users are blindly approving mobile auth requests, even when prompted repeatedly. Attackers exploit this with stolen credentials and brute-force MFA prompts.
Implement number matching, rate limiting, and delayed-prompt reviews. Reinforce “deny unless expected” training.
“Recovery” Plans Are Skipping Psychological Impact
Post-breach recovery focuses on logs, uptime, and press—but often skips the internal trust rebuild, employee communication, and mental fatigue of responders.
Include people-first check-ins, comms playbooks, and rest protocols in every IR plan. Cybersecurity is human resilience, too.
Daily News for Curious Minds
Be the smartest person in the room by reading 1440! Dive into 1440, where 4 million Americans find their daily, fact-based news fix. We navigate through 100+ sources to deliver a comprehensive roundup from every corner of the internet – politics, global events, business, and culture, all in a quick, 5-minute newsletter. It's completely free and devoid of bias or political influence, ensuring you get the facts straight. Subscribe to 1440 today.